Since the advent of the internet, there has been the need for a form of secure communication via the internet. With the vast growth and expansion in the use of digital space, it has become evident that, majority of the world’s population is now living online. This trend can be accessed from the year 2016 where there is a huge increased and erudition of people’s connectivity and interest in social media. Encryption is the process through which data is encoded so that it remains hidden from or inaccessible to unauthorized users. Encryption helps protect private information, sensitive data, and can enhance the security of communication between two parties.
Whereas the internet proposes a host of ways to communicate with friends, co-workers and complete strangers, it also allows third parties to intrude on those communications, as well as track online conversations and activities. Using encryption tools helps keep individuals communications secret and protect swapping activities of personal tales with a friend or transacting important business with a client. According to a 2018 North American report published by Shred-It, majority of business leaders believe data breach risks are higher when people work remotely. More specifically, 86% of C-Suite executives and 60% of small-business owners hold that view. In view of that, whether you work remotely all the time or just occasionally, data encryption helps in stopping information from falling into the wrong hands.
In Ghana however, information within the media could not be described as safe. This could endanger the life of both journalists and their sources. Moving into the telecommunication industry as well, lack of client data encryption has led to a lot of personal information theft including financial details. The state of data encryption could be described as poor and hoped that more attention is paid to protecting individual and organization information especially in an environment where misinformation is thriving. Generally, information encryption can be classified in the following form;
- Symmetric Encryption
As proposed by Milton Kazmeyer, one way around the problem of encryption is using a symmetrical encryption system. This involves a single cryptographic key, known to both parties, that can encrypt and decrypt information. One example of an extremely simple symmetric key is replacing letters with numbers thus,1 for “A,” 2 for “B” and so on. As long as both parties know the key, they can send secure messages back and forth. This requires a secure method for sharing the key in the first place, something that may not be possible when communicating via the internet.

Source=google images
- Public Key Encryption
Most encryption structures on the internet use a system known as public key encryption. This system encompasses a special pair of keys; one public and one private for each user, so that a user encodes messages using this pair of keys, and the other user has the opposing pair of keys for decoding the messages. For example, one user encodes a message with his private key and his correspondent’s public key, and that correspondent then decodes the message with her private key and the sender’s public key. This ensures that only the two users can gain access to the encrypted data.
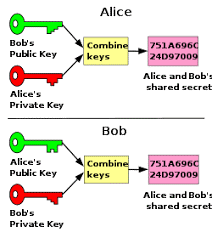
Source=google images.
- SL/TLS
Key encryption lies at the heart of Secure Sockets Layer, which is another common form of encryption on the Internet. In an SSL connection, your computer and the target computer take the roles of the two correspondents, swapping public keys and encoding all data that travels back and forth between the two machines. This ensures that file transfers and other communications remain secure, although outsiders may still be able to determine the nature of the transfer by looking at public packet information, a packet’s destination port, for example, may give away the type of transfer, as most internet protocols use easily identifiable port numbers. The Transport Layer Security, or TLS, protocol is SSL’s successor, although many users and programs refer to any such encrypted connection simply as “SSL.”
Profitably, even when not required to encrypt data due to privacy regulations, some companies choose to do so to show their clients they take privacy seriously. Making that claim is particularly important due to the eroding trust many people have in the internet. According to the 2019 CIGI-Ipsos Global Survey on Internet Security and Trust, 53% of respondents said they were more concerned about online privacy now than a year ago. The same survey indicated that nearly half of those surveyed (49%) said that their distrust of the internet made them disclose less personal information online. Surprisingly, only 19% of people surveyed said they used more encryption to increase safety. Those findings open an opportunity for companies to bolster consumer trust by explicitly stating how they encrypt customer data. Although end-users need to take responsibility as well, enterprises can solidify their reputations by stressing on a commitment to integrating the latest encryption technologies into their operations.
According to an article written by Anna Higgins, perhaps in an environment where misinformation is becoming rampant, the only way for journalists to communicate with sources via the internet is through encryption. She suggested End-to-End (E2E) encryption as a tool that keeps digital communications private by scrambling content so that only the sender and receiver have the keys to unscramble and read it. Journalists often rely on secure communication services like E2E messaging apps to connect with sources in a trustworthy way.
Ann emphasized by saying “E2E encrypted messaging apps are especially important for the safety of investigative journalists and their sources. Whistleblowers often feel safe coming forward with information if they know that their communications are completely private and secure. These individuals are often at risk of compromising their jobs and reputations by tipping off news organizations. Secure communications between journalists and whistleblowers can help protect both parties when revealing the truth and holding institutions and individuals accountable. Encryption also promotes a more trusting relationship between news organizations and their readership. Without encryption, our most reliable sources of information are in jeopardy. Without encryption, our free press cannot do their jobs to dig for the truth, keep us informed, and hold institutions and individuals accountable. Without encryption, we could be fooled into thinking that a spoof site is genuine.”
In conclusion, it is very clear that there is the need for information encryption in the internet era. Encryption is needed in every field and profession and in an environment where majority of the world’s population stores their details online, there needs to be a public education on how to keep that information safe especially from hackers and others that may use them as a means to an end.
Article by: Theorose Elikplim Dzineku.
ISOC Ghana Chapter Member.











